Using Ruckus AP Ports for tunnelling and dynamic VLANs
Introduction
One of the great aspects of Ruckus APs is that whilst you can tunnel wireless traffic back to the controller, if necessary you can do likewise for the ethernet ports as well. This is particularly useful with hospitality APs such as the H510 or H320 where the ports are likely to be used by end customers. The specific configuration in this guide is based off a couple of deployments that used the RG Nets rXg for authentication and dynamic VLAN assignment via a tunnel back to a SmartZone controller.
Requirements
No specific requirements here but we always recommend keeping your equipment up to date (check Ruckus support for recommended firmware versions).
Configuration
First of all, on your SmartZone, browse to Services & Profiles > Tunnels & Ports. Here you will see an Ethernet Port tab, so click on this:
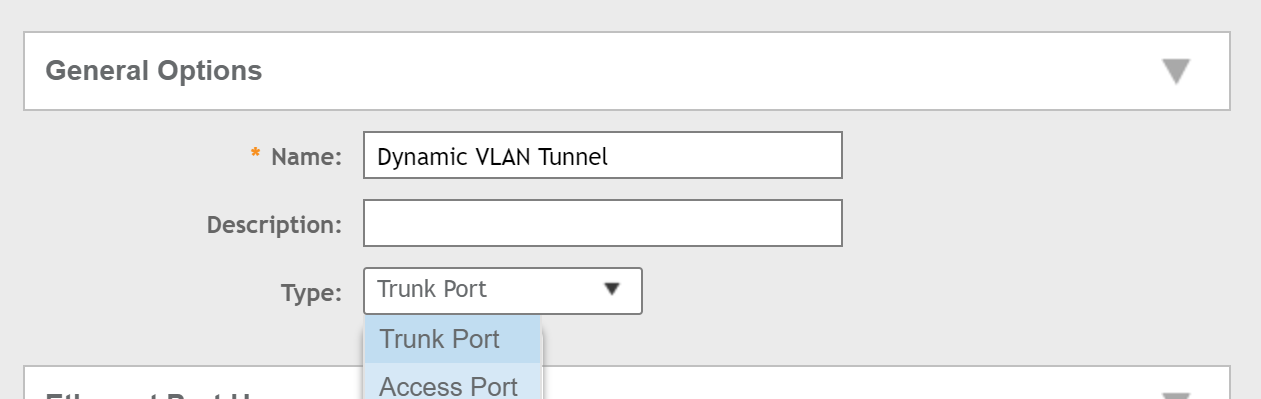
Next, ensure you are in the correct Zone and then hit the Create button. This will open a pop-up window. In the General Options section, name your profile, and then ensure you select Access Port as the Type:
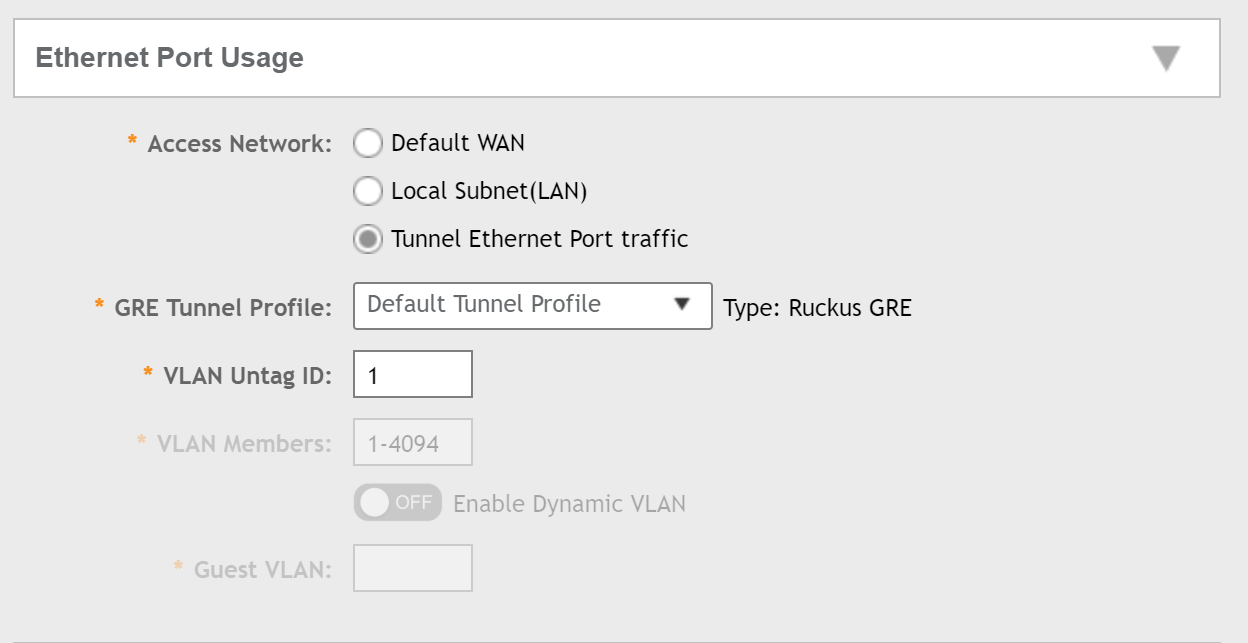
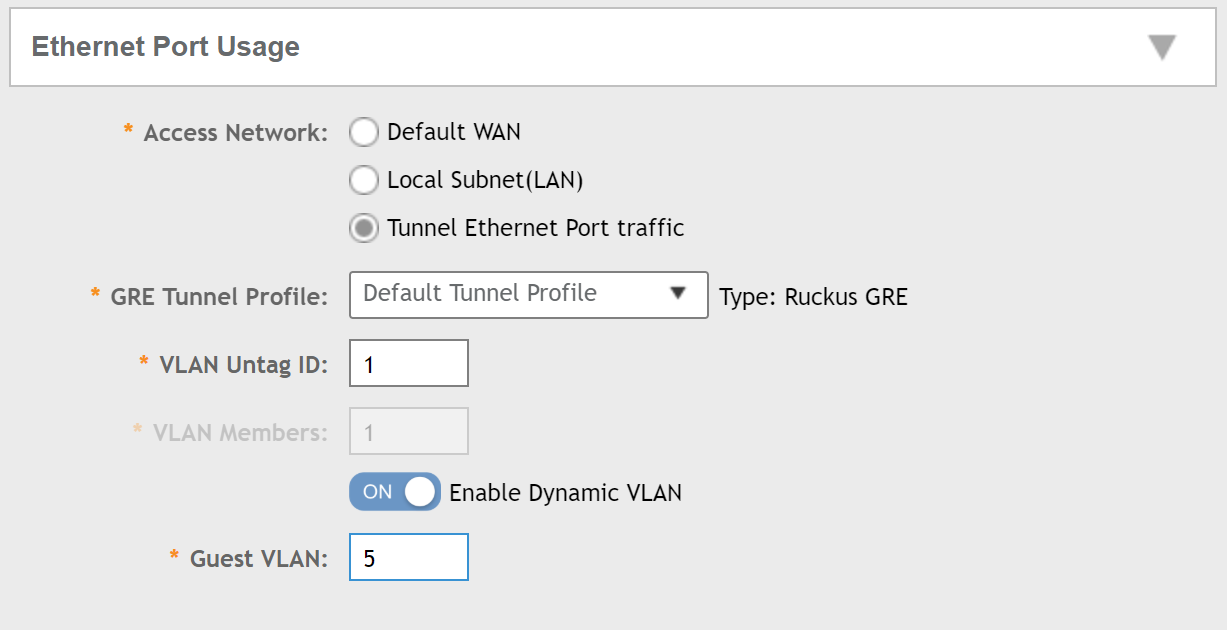
Next, select the Tunnel Ethernet Port traffic option under Ethernet Port Usage, and if you have created a separate tunnel profile, select that from the GRE Tunnel Profile dropdown:
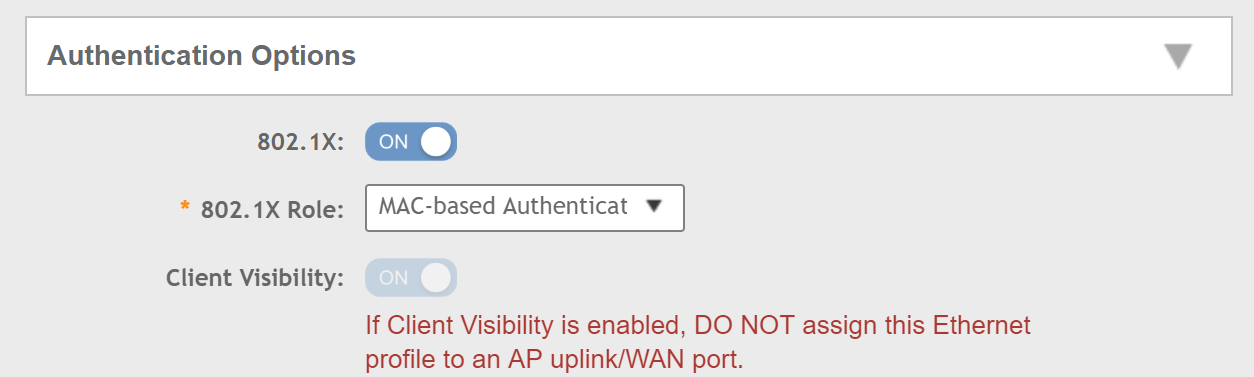
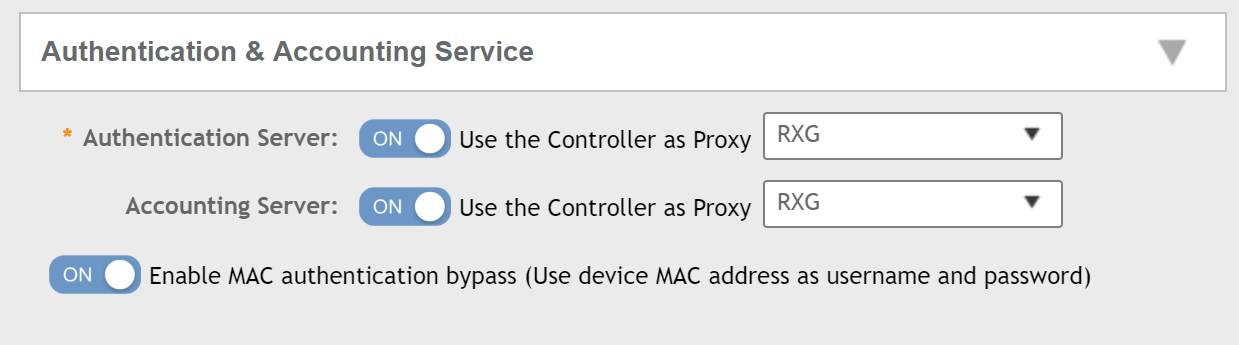
Under Authentication Options, enable 802.1X and select the role as MAC-based Authenticator:
Now select your authentication service (an rXg in the example below but can be other RADIUS servers); ensure that you enable MAC authentication bypass:
Now go back up to the Ethernet Port Usage section and you should find the Enable Dynamic VLAN option is available. Enable this, and then you will need to enter a guest VLAN (this could be an onboarding VLAN as an example).
Now hit Ok, and you should then be able to apply this profile to any AP ports that need to tunnel users back to the controller, and assign VLANs to the users dynamically.